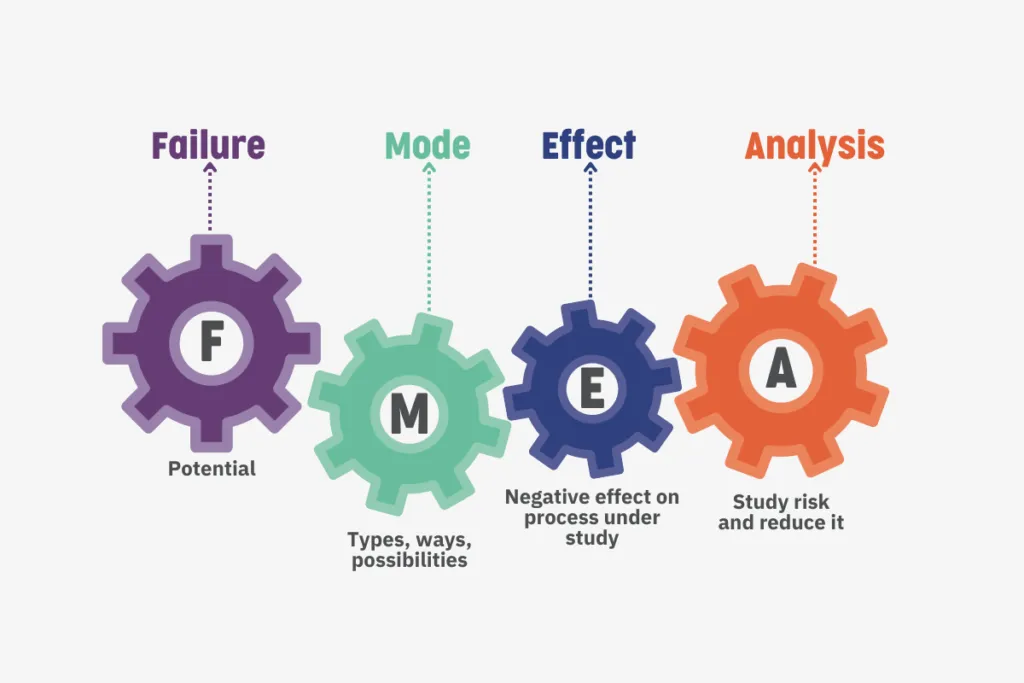
Failure Mode and Effect Analysis (FMEA) in Databases
Failure Mode and Effect Analysis (FMEA) is a systematic and proactive approach to identifying and mitigating potential failures in systems. While traditionally applied to manufacturing and engineering processes, FMEA is increasingly gaining importance in the realm of database management. FMEA in databases involves a structured analysis of potential failure modes, their effects on the system, and the severity of those effects. By understanding and prioritizing failure modes, database administrators can develop strategies to enhance the reliability and robustness of database systems.
Failure Mode and Effect Analysis (FMEA) in Databases
The FMEA process in databases typically follows a series of steps. The first step is to identify and list all possible failure modes that could occur in the database system. These failure modes can range from hardware failures and software glitches to human errors and external threats. Through brainstorming sessions and historical data analysis, a comprehensive list of potential failure modes is compiled.
Once the failure modes are identified, the next step is to assess the severity of each potential failure’s impact on the database system. This involves considering how each failure mode could affect data integrity, system performance, and overall functionality. Severity rankings help prioritize which failure modes require immediate attention and mitigation efforts.
After assessing severity, the FMEA process involves evaluating the likelihood or probability of each failure mode occurring. This step considers factors such as the frequency of specific events, the reliability of hardware and software components, and the effectiveness of existing preventive measures. By assigning probability rankings, administrators can focus on addressing the most likely sources of failure.
The final step in the FMEA process is determining the detectability of each failure mode. Detectability assesses the likelihood of identifying a failure mode before it leads to significant consequences. Factors such as monitoring tools, alert systems, and human oversight contribute to the detectability rating. By understanding how easily a failure mode can be detected, administrators can implement measures to enhance monitoring and detection capabilities.
The product of these assessments is the Risk Priority Number (RPN), calculated by multiplying the severity, probability, and detectability rankings for each failure mode. The higher the RPN, the higher the priority for addressing that specific failure mode. This prioritization allows administrators to focus their resources on the most critical aspects of database reliability.
The application of FMEA in databases is not without challenges. It requires collaboration between different stakeholders, including database administrators, IT professionals, and domain experts. Gathering accurate data for probability and detectability assessments can also be challenging, especially in dynamic and evolving database environments.
Failure Mode and Effect Analysis (FMEA) in databases is a valuable tool for proactively identifying and mitigating potential failures. By systematically assessing the severity, probability, and detectability of failure modes, administrators can prioritize efforts to enhance the reliability and resilience of database systems. As databases continue to play a central role in various industries, the application of FMEA will likely become increasingly crucial for maintaining data integrity and system functionality.
FMEA Process in Database Management
The Failure Mode and Effect Analysis (FMEA) process is a structured and systematic approach to identifying and prioritizing potential failures in a system and understanding their potential impacts. In the realm of database management, FMEA is a valuable tool for enhancing the reliability, performance, and resilience of database systems. The FMEA process in database management involves a series of steps, from identifying potential failure modes to prioritizing mitigation strategies.
- Identification of Failure Modes: The first step in the FMEA process is to identify and list all possible failure modes that could occur in the database system. This step often involves brainstorming sessions, reviews of historical data, and input from subject matter experts. Failure modes can encompass a wide range of issues, including hardware failures, software glitches, data corruption, human errors, and external security threats.
- Assessment of Severity: Once the failure modes are identified, the next step is to assess the severity of each potential failure’s impact on the database system. This involves considering the consequences of each failure mode in terms of data integrity, system performance, and overall functionality. Severity assessments help prioritize which failure modes require immediate attention and mitigation efforts.
- Evaluation of Probability: The FMEA process then involves evaluating the likelihood or probability of each failure mode occurring. This step considers factors such as the frequency of specific events, the reliability of hardware and software components, and the effectiveness of existing preventive measures. Probability assessments help administrators focus on addressing the most likely sources of failure.
- Determination of Detectability: Detectability assesses the likelihood of identifying a failure mode before it leads to significant consequences. This step considers the effectiveness of monitoring tools, alert systems, and human oversight in detecting potential issues. Detectability assessments help administrators understand how easily a failure mode can be detected and addressed.
- Calculation of Risk Priority Number (RPN): The final step in the FMEA process is determining the Risk Priority Number (RPN) for each failure mode. The RPN is calculated by multiplying the severity, probability, and detectability rankings assigned to each failure mode. This numerical value provides a quantitative measure of the risk associated with each failure mode. The higher the RPN, the higher the priority for addressing that specific failure mode.
- Prioritization and Mitigation Strategies: Based on the RPN values, administrators can prioritize their efforts to address the most critical failure modes. High-priority failure modes may require immediate attention and the implementation of mitigation strategies. These strategies could include hardware or software upgrades, enhanced monitoring systems, training programs, or changes to operational procedures.
The FMEA process in database management is an iterative one, as databases evolve and new potential failure modes emerge. Regular reviews and updates to the FMEA help ensure that database administrators stay proactive in addressing risks and maintaining the reliability of database systems.
Challenges in the FMEA process in database management include the need for accurate data, collaboration among different stakeholders, and the dynamic nature of database environments. Despite these challenges, the systematic and structured approach of FMEA provides a valuable framework for enhancing the reliability and robustness of database systems.
The FMEA process in database management is an invaluable tool for proactively identifying and mitigating potential failures. By systematically assessing the severity, probability, and detectability of failure modes, administrators can prioritize efforts to enhance the reliability and resilience of database systems, ultimately contributing to the stability and dependability of data management across various industries.
Database Failure Modes and Effects
Database failure modes and their effects can have profound consequences on the reliability, performance, and integrity of data management systems. Understanding and mitigating these failure modes are crucial for ensuring the smooth operation of databases, especially in industries where data is a critical asset. Common database failure modes encompass a range of issues, from hardware and software failures to human errors and security breaches, each with its unique effects on the system.
- Hardware Failures: Hardware failures represent a significant category of database failure modes. These failures can include issues with storage devices, memory modules, processors, and other physical components. The effects of hardware failures can range from data corruption and loss to system crashes and downtime. Implementing redundant hardware configurations and regular monitoring can help mitigate the impact of hardware failures.
- Software Glitches and Bugs: Software failures, such as glitches and bugs in the database management system (DBMS) or application software, can lead to unexpected behavior and data inconsistencies. The effects may include data corruption, system instability, and disruptions in data processing. Regular software updates, testing, and quality assurance practices are essential for minimizing the occurrence of software-related failures.
- Data Corruption: Data corruption is a failure mode with severe consequences for database integrity. It can result from various factors, including hardware malfunctions, software errors, or issues during data transmission. The effects of data corruption include inaccurate or incomplete data, leading to potential errors in decision-making and analysis. Implementing robust backup and recovery strategies is critical for mitigating the impact of data corruption.
- Human Errors: Human errors, such as accidental deletion of records, misconfigurations, or unauthorized access, represent a common and impactful failure mode in databases. The effects can include data loss, privacy breaches, and compromised system security. Training programs, access controls, and audit trails are essential components for reducing the likelihood and impact of human errors.
- Security Breaches: Security breaches, including unauthorized access, data breaches, and cyberattacks, pose significant threats to database systems. The effects of security breaches extend beyond data loss and can include reputational damage, legal consequences, and financial losses. Implementing robust security measures, encryption, and regular security audits are critical for safeguarding databases against malicious activities.
Understanding the effects of these failure modes allows database administrators to implement strategies for prevention, detection, and recovery. The goal is not only to minimize the occurrence of failures but also to enhance the resilience of database systems when failures do occur.
Mitigation strategies for database failure modes include:
- Redundancy and Backups: Implementing redundant hardware components and maintaining regular backups help ensure data availability and recoverability in the event of failures.
- Monitoring and Alerts: Continuous monitoring of database performance and the implementation of alert systems enable administrators to detect and respond to potential issues promptly.
- Access Controls and Authentication: Strict access controls, strong authentication mechanisms, and proper user permissions help mitigate the impact of human errors and unauthorized access.
- Security Measures: Robust security measures, including encryption, firewalls, and intrusion detection systems, protect databases from security breaches and cyber threats.
Risk Analysis in Database Systems
Risk analysis in database systems is a critical process that involves identifying potential threats, vulnerabilities, and uncertainties that may impact the security, performance, and integrity of data. As databases become central to the functioning of organizations across various industries, understanding and mitigating risks is paramount. Risk analysis provides a structured framework for assessing, prioritizing, and managing risks, enabling organizations to make informed decisions and implement effective mitigation strategies.
The process of risk analysis in database systems typically involves several key steps:
- Identification of Assets: The first step is to identify and inventory the assets within the database system. This includes data, hardware, software, personnel, and any other components that contribute to the functionality and security of the database. Understanding the value and criticality of these assets is essential for prioritizing risk mitigation efforts.
- Threat Identification: The next step is to identify potential threats to the database system. Threats can come from various sources, including external attackers, internal users, natural disasters, and technological failures. By categorizing and understanding potential threats, organizations can assess the likelihood of each threat occurring and its potential impact on the database.
- Vulnerability Assessment: Vulnerability assessment involves identifying weaknesses and vulnerabilities in the database system that could be exploited by threats. This includes assessing the security of hardware, software configurations, access controls, and network infrastructure. Identifying vulnerabilities helps organizations understand the avenues through which threats may exploit the system.
- Risk Assessment: Risk assessment combines the likelihood of a threat occurring with the potential impact on the database system to determine the overall risk. This involves assigning qualitative or quantitative values to the likelihood and impact, resulting in a risk score. High-risk areas require immediate attention and mitigation.
- Prioritization and Mitigation Strategies: Based on the results of risk assessment, organizations can prioritize their efforts and focus on mitigating high-priority risks. Mitigation strategies may include implementing security controls, enhancing access management, conducting regular security audits, and establishing disaster recovery plans.
- Monitoring and Review: Continuous monitoring and regular reviews are crucial components of risk analysis in database systems. Threat landscapes evolve, and new vulnerabilities may emerge. Ongoing monitoring allows organizations to adapt their risk mitigation strategies to address emerging threats and changes in the database environment.
Challenges in risk analysis in database systems include the dynamic nature of technology, evolving threat landscapes, and the need for interdisciplinary collaboration. Addressing these challenges requires a holistic and proactive approach to risk management, where organizations continuously assess, adapt, and improve their security measures.
Risk analysis in database systems is a foundational practice for organizations seeking to safeguard their data, maintain system integrity, and ensure the resilience of their database infrastructure. By systematically identifying and mitigating risks, organizations can make informed decisions, enhance their security posture, and protect critical information assets.
FMEA Implementation in Data Integrity
Failure Mode and Effect Analysis (FMEA) is a systematic method for identifying and prioritizing potential failure modes in a process, product, or system and assessing their effects. When applied to data integrity, FMEA becomes a powerful tool for understanding and mitigating the risks associated with data inaccuracies, corruption, and loss within databases. FMEA implementation in data integrity involves a structured analysis of potential failure modes, their causes, effects, and the development of strategies to enhance the accuracy and reliability of data.
The implementation of FMEA in data integrity typically follows these key steps:
- Identification of Data Integrity Objectives: Before delving into FMEA, organizations need to define their data integrity objectives. This involves understanding the criticality of data, defining accuracy requirements, and establishing the desired level of reliability. Clear objectives provide a foundation for the FMEA process.
- Formation of Cross-Functional Teams: FMEA is most effective when performed by cross-functional teams that bring together individuals with diverse expertise, including database administrators, data analysts, subject matter experts, and end-users. This collaborative approach ensures a comprehensive analysis of potential failure modes.
- Identification of Data Failure Modes: The team systematically identifies potential failure modes related to data integrity within the database. This could include errors during data entry, software bugs, hardware failures, or issues with data migration and integration. Each failure mode is documented along with its potential causes.
- Assessment of Severity, Occurrence, and Detectability: For each identified failure mode, the team assesses its severity (impact on data integrity), occurrence (likelihood of the failure mode occurring), and detectability (likelihood of detecting the failure mode before it causes significant issues). These assessments are typically scored on a numerical scale.
- Calculation of Risk Priority Number (RPN): The Risk Priority Number (RPN) is calculated by multiplying the severity, occurrence, and detectability scores for each failure mode. The RPN helps prioritize which failure modes require immediate attention and mitigation efforts. High RPN values indicate higher-risk areas.
- Development of Mitigation Strategies: Based on the RPN values, the team develops mitigation strategies for high-risk failure modes. These strategies could involve implementing data validation checks, improving data entry processes, enhancing software testing procedures, or establishing backup and recovery mechanisms. The goal is to reduce the likelihood and impact of potential data failures.
- Implementation and Monitoring: The identified mitigation strategies are implemented, and the team monitors their effectiveness over time. Continuous monitoring and periodic reviews ensure that the implemented measures remain effective and relevant as the database environment evolves.
Challenges in FMEA implementation in data integrity include the complexity of database systems, the dynamic nature of data, and the need for ongoing collaboration and communication among team members. Overcoming these challenges requires a commitment to continuous improvement and a proactive approach to data integrity management.
In conclusion, FMEA implementation in data integrity is a valuable process for organizations seeking to enhance the reliability and accuracy of their databases. By systematically analyzing potential failure modes and implementing targeted mitigation strategies, organizations can minimize the risks associated with data integrity issues, ensuring the trustworthiness of critical information assets.
FMEA for Database Security
Failure Mode and Effect Analysis (FMEA) applied to database security is a systematic and proactive approach to identifying and mitigating potential security risks and vulnerabilities within a database system. As databases store sensitive and critical information, ensuring robust security measures is paramount. FMEA for database security involves a structured analysis of potential failure modes related to security, their causes, effects, and the development of strategies to strengthen the security posture of the database.
The implementation of FMEA for database security typically involves the following key steps:
- Definition of Security Objectives: Before initiating the FMEA process, organizations need to clearly define their database security objectives. This involves understanding the sensitivity of the data, regulatory requirements, and the desired level of confidentiality, integrity, and availability. Clear objectives provide a foundation for the security-focused FMEA.
- Formation of Cross-Functional Security Teams: Security FMEA is most effective when performed by cross-functional teams comprising individuals with expertise in database administration, cybersecurity, risk management, and compliance. This collaborative approach ensures a comprehensive analysis of potential security failure modes.
- Identification of Security Failure Modes: The team systematically identifies potential security failure modes within the database system. This could include unauthorized access, data breaches, SQL injection attacks, malware infections, or issues with encryption protocols. Each security failure mode is documented along with its potential causes.
- Assessment of Severity, Occurrence, and Detectability: For each identified security failure mode, the team assesses its severity (impact on security), occurrence (likelihood of the security failure mode occurring), and detectability (likelihood of detecting the security failure mode before it causes significant issues). These assessments are typically scored on a numerical scale.
- Calculation of Risk Priority Number (RPN): Similar to FMEA for data integrity, the Risk Priority Number (RPN) is calculated by multiplying the severity, occurrence, and detectability scores for each security failure mode. The RPN helps prioritize which security failure modes require immediate attention and mitigation efforts. High RPN values indicate higher-risk areas.
- Development of Mitigation Strategies: Based on the RPN values, the team develops targeted mitigation strategies for high-risk security failure modes. These strategies could involve implementing access controls, conducting regular security audits, patching vulnerabilities, educating users on security best practices, and implementing intrusion detection systems. The goal is to reduce the likelihood and impact of potential security failures.
- Implementation and Continuous Improvement: The identified mitigation strategies are implemented, and the team monitors their effectiveness over time. Continuous monitoring, regular security assessments, and periodic reviews ensure that the implemented measures remain effective and adapt to the evolving threat landscape.
Challenges in FMEA for database security include the sophistication of cyber threats, the rapid evolution of attack vectors, and the need for ongoing training and awareness among database administrators and users. Overcoming these challenges requires a proactive and adaptive approach to database security management.
FMEA for database security is a valuable process for organizations seeking to enhance the resilience and robustness of their database security measures. By systematically analyzing potential security failure modes and implementing targeted mitigation strategies, organizations can minimize the risks associated with security breaches, ensuring the confidentiality and integrity of critical information assets.
Understanding the various failure modes and their effects is fundamental to maintaining the reliability and integrity of database systems. By proactively addressing these failure modes through mitigation strategies and best practices, administrators can ensure the continuous and secure operation of databases, safeguarding critical data and supporting the needs of diverse industries.